Thursday, December 22, 2011
LogMeIn Free App for iPad & iPhone Remote PC Access
If you need remote access to your desktop from your iPad or iPhone, now you can get access for free. LogMeIn has a new app in the Apple App Store and it is free. Prior to today the price of admission was $30 for their Ignition app. Although the new app doesn't offer everything that the current paid app provides such as: file management; cloud storage; HD video/audio streaming, if you just need remote access the free App works very well. Access is easy. From your Desktop PC go to www.LogMeIn.com and setup an Account for Free. Then, go to the Apple App Store and download the Free app. If you have already paid for the Ignition app you will be grandfathered in and have access to the premium features.
LinkedIn Profile
Wednesday, December 14, 2011
Important Patches are released!
Microsoft’s “Patch Tuesday” for December has arrived and it is substantial. The updates included in this patch are for repair of twenty issues including a fix for the dangerous Duqu worm that took the internet by storm recently. In addition, the browser exploit against SSL/TSL cookies (BEAST) is being fixed in this package.
Three updates are critical and affect Windows XP, Vista and windows 7. Five of the important bulletins affect Office 2003, 2007 and 2010 including all office versions for Macintosh as well. In addition users of Adobe 9 can expect an update that will address the current 0-day vulnerability in Reader.
For more information Click Here
Monday, December 12, 2011
iPad for Lawyers CLE Seminar
_________________________________________________________________________________
CLE Seminar Dates:
• Thursday January 26th - 8:30am-10am
• Tuesday February 7th - 5:00pm-6:30pm
_________________________________________________________________________________
Unleash the Power of your iPad
Untether yourself from the office and increase productivity and billable hours. Learn how to use the iPad for document creation, collaboration, legal research, connecting to your office, as well as applications that are legal specific and so much more... Current and prospective iPad owners will walk away empowered to increase their productivity immediately.
Some of the topics include:
• best apps for attorneys
• courtroom applications
• legal research
• hardware and web browsing tips
• managing mail, calendar and contacts
• multitasking and iTunes
• adding files and synching
• document creation
• connecting to your office
This class gives you 1 1/2 CLE credits.
To sign up Contact Maureen at the Nassau County Bar Association Tech Center: (516) 747-4464 ext 228
_________________________________________________________________________________
Saturday, December 10, 2011
Adobe Acrobat Flaw Targeting Computers
 ADOBE ACROBAT ALERT
ADOBE ACROBAT ALERTA vulnerability in Adobe Acrobat is being exploited in targeted attacks against telecommunications, manufacturing, computer hardware, chemical and defense sector companies.
Be wary of suspicious emails that arrive in your email with PDF attachments. By opening the PDF attachment your computer gets infected with information stealing malware.
Adobe is working on a Patch to correct the problem. This issue affects all current versions of Reader and Acrobat. Here is a link to the Adobe Security Advisory they issued.
Inform all users to be very careful with PDF files that come from outside your organization, whether from a trusted source or not.
We will let you know when Adobe Releases an update to Resolve the Issue.
Wednesday, November 9, 2011
Amicus Attorney Premium Edition 2001 SP1 is now available!
If you have Amicus Attorney Premium Edition 2011, a cumulative patch has been release that will fix a number of issues affecting Amicus Attorney including those listed below:
- TIME: Time Entries on Non-billable File are included in Billable time in Statistics view.
- TIME: If File is assigned a custom Billing Category, wrong Category might be assigned in Time Entries.
- CALENDAR: Documents and e-mails cannot be associated to Event from Event Details.
- REPORTS: Non-billable Time Entries on Billable File are included in Billable time in Basic and Advanced reports.
- AMICUS PREMIUM BILLING -CLIENTS: Opening Client Details might cause exception error.
- AMICUS PREMIUM BILLING - QUICKBOOKS LINK: Trust transactions might fail to exchange to QuickBooks.
- AMICUS SMALL FIRM ACCOUNTING INTEGRATION: New File creation in Amicus Attorney might fail.
- TIMESLIPS LINK: Category in Time Entry cannot be changed to "No Charge", "Do Not Bill", "Hold-Billable".
If you would like to go ahead and download this patch yourself the link is: Amicus Attorney Premium Edition 2011 SP1 Patch We are always happy to assist you with when applying patches, so please do not hesitate to call us to assist you in this process. You can reach Glasser Tech at 516-762-0155.
A couple of things to note about this patch:
- Unlike a regular Service Pack, this patch is not available from the InstallShield Updater Site. It is only available from the webpage noted above.
- It is applicable only to those running Amicus Attorney Premium Edition 2011 SP1 with or without Amicus Premium Billing 2011.
- It must be applied to the Amicus Server and to each Amicus Workstation. The patch installer ensures that this process is simple, fast and ensures that it cannot be installed only in an environment running SP1.
- A communication to all Amicus Attorney Premium Edition 2011 customers will be sent on Monday, November 7th advising them that the Patch is available.
For your software to be most efficient it is important that this patch be installed. Call for assistance today! 516-762-0155.
Tuesday, November 8, 2011
Microsoft Patch Day
It’s Microsoft Patch Day again. As expected, today's Patch Day has a Windows theme, since all of Microsoft's security bulletins affect Windows or components that ship with it. More importantly, most of the updates primarily affect modern versions of Windows, such as Windows Vista, 7, or Server 2008; only one of the Important bulletins affect older versions of Windows.
If you feel that you need assistance when applying Microsoft updates, please call us at 516-762-0155.
Bulletins Affect TCP/IP, Active Directory, Windows Mail, and More
Severity: High
Summary:
· These vulnerabilities affect: All current versions of Windows and components that ship with it (though most only affect more recent versions of Windows)
· How an attacker exploits them: Multiple vectors of attack including sending specially crafted packets, or enticing users into opening booby-trapped files
· Impact: Various results; in the worst case, an attacker can gain complete control of your Windows computer
· What to do: Install the appropriate Microsoft patches immediately, or let Windows Automatic Update do it for you.
Exposure:
Today, Microsoft released four security bulletins describing four vulnerabilities that affect Windows and components that ship with it. Each vulnerability affects different versions of Windows to varying degrees, with most of this month's bulletins affecting Windows Vista, 7, and Server 2008. A remote attacker could exploit the worst of these flaws to gain complete control of your Windows PCs. The summary below lists the vulnerabilities, in order from highest to lowest severity.
· MS11-083: TCP/IP Remote Code Execution Vulnerability
As you would expect, the Windows TCP/IP stack is a set of networking protocols that allows your computer to get on the Internet and participate in modern networking. Unfortunately, the Windows TCP/IP stack suffers from an i nteger overflow flaw involving its inability to properly parse a continuous flow of specially crafted UDP packets. By sending such packets, an attacker could leverage this flaw to gain complete control of your Windows computer. This flaw only affects Windows Vista, 7, and the Server 2008 versions of Windows. That said, this is a seriously vulnerability, and we recommend you patch it immediately.
Microsoft rating: Critical
· MS11-085: Windows Mail and Meeting Space Insecure Library Loading Vulnerability
Windows Mail is the default email client that ships with Windows and Meeting Space is a built in document and desktop sharing application. Unfortunately, both these components suffers from the insecure Dynamic Link Library (DLL) loading class of vulnerability that we've described in many previous Microsoft alerts. In a nutshell, this class of flaw involves an attacker enticing one of your users into opening some sort of booby-trapped file from the same location as a specially crafted, malicious DLL file. If you do open the booby-trapped file, it will execute code in the malicious DLL file with your privileges. If you have local administrative privileges, the attacker could exploit this type of issue to gain complete control of your computer. In this particular case, the vulnerability is triggered by files types associated with Mail and Meeting Space--specifically .EML and .WCINV files.
Microsoft rating: Important.
· MS11-086: Active Directory Elevation of Privilege Vulnerability
Active Directory (AD) provides central authentication and authorization services for Windows computers and ships with server versions of Windows. Among its many options, AD allows you to authentication using certificates. AD suffers from a certificate handling vulnerability when configured to use LDAP over SSL (LDAPS). In short, AD doesn't properly recognize revoked SSL certificates, which means an attacker can use a revoked certificate to authenticate and possibly gain access to your systems. However, the attacker would first have to somehow gain access to the revoked certificate for a valid account on your domain to leverage this flaw, which significantly mitigates its severity. If an attacker has access to valid account certificates, revoked or not, you already have a serious problem on your hands.
Microsoft rating: Important.
· MS11-084: Kernel-mode Driver Denial of Service Vulnerability
The kernel is the core component of any computer operating system. Windows also ships with a kernel-mode device driver (win32k.sys) which handles many kernel-level devices. The kernel-mode driver suffers from a Denial of Service (DoS) vulnerability involving the way it handles specially crafted TrueType font files. By enticing one of your users to open a specially crafted font file, or to browse to a share hosting such a file, an attacker could exploit this flaw to cause your system to stop responding, until you restart it. This flaw only affects Windows 7 and Server 2008 R2.
Microsoft rating: Moderate.
Solution Path:
Microsoft has released patches for Windows which correct all of these vulnerabilities. You should download, test, and deploy the appropriate patches throughout your network immediately. If you choose, you can also let Windows Update automatically download and install these for you.
· For Windows Vista x64 (w/SP2)
· For Windows Server 2008 (w/SP2)
· For Windows Server 2008 x64 (w/SP2)
· For Windows Server 2008 Itanium (w/SP2)
· For Windows Server 2008 R2 x64 (w/SP1)
· For Windows Server 2008 R2 Itanium (w/SP1)
· For Windows Vista x64 (w/SP2)
· For Windows Server 2008 (w/SP2) *
· For Windows Server 2008 x64 (w/SP2) *
· For Windows Server 2008 Itanium (w/SP2)
· For Windows Server 2008 R2 x64 (w/SP1) *
· For Windows Server 2008 R2 Itanium (w/SP1)
* Server Core installations not affected: If you chose the "Server Core" installation option, Windows does not install unnecessary client applications, such as Mail or Meeting Space.
Active Directory updates:
· For Windows Server 2003 (w/SP2)
o Active Directory Application Mode (ADAM)
· For Windows Server 2003 x64 (w/SP2)
o Active Directory Application Mode (ADAM)
· For Windows Server 2003 Itanium (w/SP2)
· For Windows Vista x64 (w/SP2)
· For Windows Server 2008 (w/SP2)
· For Windows Server 2008 x64 (w/SP2)
· For Windows Server 2008 R2 x64 (w/SP1)
· For Windows Server 2008 R2 Itanium (w/SP1)
Friday, October 28, 2011
Important Timeslips Update!
Timeslips Version 2011 and Version 2012 recently had an Important Update Released.
It is Critical that all users of Timeslips Version 2011 as well as Timeslips Version 2012 install this update.
Call Glasser Tech at 516-762-0155 to schedule your update.
Wednesday, October 19, 2011
Don’t be afraid to switch to Android!
by Adam Schultz
I’ve had a blackberry phone with AT+T for the last 10 years. Over the last several months, I’ve been having trouble with dropping calls, very poor reception and extremely slow web browsing.
I tried replacing the SIM card and wiping out all the data on the blackberry but still had the same issues.
I was due for an upgrade so when I went to the AT+T store and asked for a new phone. They recommended getting an Android phone. I was hesitant, at first, because I’ve had the blackberry for so long and was afraid of trying something new. But when the AT+T sales rep told me that she also had just recently switched over from a blackberry to an android phone and loved her new phone, I decided it was time I faced my fears.
I have had the new Samsung Galaxy s2 phone for a few weeks now and I couldn’t be happier. I have yet to drop a call, even while driving! The service across Long Island, so far, has been much better that it had been with my old blackberry. The 4.3” screen is so bright and clear. There are thousands of apps to download, all at the touch of a button. It was very easy to add both work and personal email accounts. The browsing speed is incredibly fast and I love that there is an 8mp camera and that you can video record at 1080p in full HD. You can make calls, send messages, schedule appointments and launch apps with the ease of voice commands. My only regret is that I did not switch to an Android sooner. I love my new Samsung Galaxy s2 and highly recommend it to anyone looking for a new phone. It will make you forget you ever had a blackcherry or quackberry or whatever it’s called.
Tuesday, October 11, 2011
October 11, 2011 Today is Microsoft Patch Day!
In an effort to keep your computers from being hacked Microsoft is releasing today, in it’s monthly series of patches, 8 separate security fixes to patch 23 holes in a key range of their products. Some of these fixes are deemed critical as they will stop hackers from remotely running code in Windows, Internet Explorer, .NET and Silverlight.
Another bulletin, marked as important, addresses flaws in components found only on 32-bit and 64-bit versions of Windows Vista and Windows 7, while there are two more that affect all versions of Microsoft's operating system.
One bulletin patches vulnerabilities in Microsoft Forefront Unified Access Gateway, one of the company's secure remote access lashups. The versions affected are 2010, 2010 Update 1, 2010 Update 2 and 2010 Service Pack 1.
There is also a fix for elevation of privilege (EoP) flaws in Windows XP and Windows Server 2003, while the other addresses a denial of service (DoS) condition in the Microsoft Host Integration Server 2004 SP1, 2006 SP1, 2009 and 2010.
Users with Windows Update enabled to "install updates automatically" will receive the critical patches by default and can decide if they want to install the important updates.
Thursday, September 15, 2011
Reader and Acrobat Updates Correct 13 Security Flaws
Summary:
· This vulnerability affects: Adobe Reader and Acrobat X 10.1 and earlier, on Windows, Mac, as well as Reader 9.4.2 for UNIX
· How an attacker exploits it: Typically, by enticing your users into viewing a maliciously crafted PDF document
· Impact: In the worst case, an attacker can execute code on your computer, potentially gaining control of it
· What to do: Install Adobe's Reader and Acrobat X 10.1.1 update as soon as possible (or let Adobe's Updater do it for you).
Exposure:
As part of their quarterly patch day cycle (which shares the same date as Microsoft Patch Day), Adobe released a security bulletin describing 13 security vulnerabilities (number based on CVE-IDs) that affect Adobe Reader and Acrobat X 10.1 and earlier, running on Windows and Mac, as well as Reader 9.4.2 for UNIX. The flaws differ technically, but consist primarily of buffer overflow and memory corruption vulnerabilities, and share the same general scope and impact.
In the worst case, if an attacker can entice one of your users into downloading and opening a maliciously crafted PDF document (.pdf), he can exploit many of these vulnerabilities to execute code on that user's computer, with that user's privileges. If your user has local administrative privileges, the attacker gains full control of the user's machine. Keep in mind, Reader installs helpers in your browser to help it view PDF documents. Simply visiting a web site with a malicious embedded PDF document could trigger this type of attack.
Lately, attackers have leveraged Reader vulnerabilities in many of their email and web-based malware campaigns. We highly recommend you patch these Reader flaws as soon as possible.
Solution Path
Adobe has released Reader and Acrobat X 10.1.1 to fix these vulnerabilities. You should download and deploy the corresponding updates immediately, or let the Adobe Software Updater program do it for you. Adobe plans to release Reader 9.4.6 for UNIX on November 7, 2011. So you UNIX users will have to wait for their patch.
· Adobe Reader X 10.1.1
o For Mac
· Adobe Acrobat X
o Standard and Pro for Windows
For All WatchGuard Users:
Many WatchGuard Firebox models can block incoming PDF files. However, most administrators prefer to allow these file types for business purposes. Nonetheless, if PDF files are not absolutely necessary to your business, you may consider blocking them using the Firebox's proxies until the patch has been installed.
If you would like to use our proxies to block PDF documents, follow the links below for instructions:
· XTM Appliance with WSM 11.x
o How do I block files with the FTP proxy?
o How do I block files with the HTTP proxy?
o How do I block files with the POP3 proxy?
o How do I block files with the SMTP Proxy?
· Firebox X Edge running 10.x
o How do I block files with the FTP proxy?
o How do I block files with the HTTP proxy?
o How do I block files with the POP3 proxy?
o How do I block files with the SMTP proxy
· Firebox X Core and X Peak running Fireware 10.x
o How do I block files with the FTP proxy?
o How do I block files with the HTTP proxy?
o How do I block files with the POP3 proxy?
o How do I block files with the SMTP proxy?
Status:
Adobe has released patches that correct these vulnerabilities.
References:
Friday, August 26, 2011
Hurricane Preparation
WHAT TO DO BEFORE THE STORM
As you know most of Long Island is preparing for Hurricane Irene. The following guidelines are suggestions for preparation of the storm with respect to your computers, servers, etc.
- Run a back up before you shut down your server so that you have a current back up.
- Any equipment close to windows should be moved to a safe location. Perhaps a closet or inside corner of a room. If equipment cannot be moved try to cover it with tape and plastic bags and/or a tarp.
- All computer equipment including PCs, servers, monitors, printers, routers, switches, phones and phone systems should be shut down and unplugged. Surge protectors and Battery Packs should be turned off and unplugged.
Please follow the order below:
- Turn off any printers.
- Save your work and turn off Desktop and Laptop Computers.
- Turn off your secondary Servers, if any, and then your Main Server.
- Turn off Back up devices.
- Turn off your network switch.
- Turn off your Firewall or Router.
- Turn off your Telephone System.
- Turn off your Internet Provider's Equipment (Cable, DSL, Satellite or T1 Modem)
- Turn off and unplug all Surge Protectors and Battery Packs for all devices.
WHAT TO DO AFTER THE STORM
Reconnecting your equipment:
- Even after the storm is over damage can still occur to your equipment due to power surges or outages while the power company begins to restore power to affected areas.
- Check to be sure your equipment has not been exposed to water. If you notice a piece of equipment has water damage, do not plug it in or turn it off. Call our office first.
- Wait until you hear from LIPA that the electrical power is stabilized in your area. Power surges and outages can do all kinds of damage. Once you know it is okay power should be restored to core systems and infrastructure first. These include routers, firewalls, switches, servers and telephone systems.
Please follow the order below:
- Plug in and turn on all Surge Protectors and Battery Packs for all devices.
- Turn on your Internet Provider's equipment (Cable, DSL, Satellite or T1 modem)
- Turn on your Network Switch.
- Turn on your Firewall or Router.
- Turn on your Telephone System.
- Turn on your Main Server first and then any other servers.
- Plug in and turn on Desktop and Laptop Computers.
- Plug in and turn on Back up Devices.
- Plug in and turn on Printers.
We hope that you take these precautions to ensure that your office is secure. Should you need our assistance, please contact us at 516-762-0155.
Sincerely,
Michael Glasser
Glasser Tech LLC
Monday, July 25, 2011
Because your Time Matters….
Time Matters is designed to make your case management quick and easy. Listed below are a few tips that you may not know about that will increase your productivity within Time Matters.
- You can save your current login information by selecting the Options button and checking “Save This Login” at the Time Matters login screen.
- Tag every item in a list all at once by using the hot keys CTRL+T to tag all records. CTRL+U to untag.
- The main “data entry forms” in Time Matters are resizable. Click and hold a corner or edge of the form, and drag the cursor to resize it.
- Quick Tabs provide you the ability to create and view filtered lists or saved searches, allowing you to see critical information at a glance saving you a lot of time. To learn about Quick Tabs go to the help section in Time Matters.
- To modify the buttons on the Main toolbar, right-click on it and click Customize.
- Archive records when they are no longer needed. Open a list, tag all unused records, and on the Main Menu go to Process > Archive Records. This is helpful if you want to hide (but not delete) inactive clients and matters.
- Almost any list can easily be sent to Excel, making it simple to print records, manipulate columns, etc. When you are on a Quick Tab, hit CTRL + T to tag all of the records in the list. Click the Send to Excel button on the list toolbar. Excel will automatically open filling in the spreadsheet with the selected information.
- Time Matters has its own Recycle Bin just for deleted records. So don’t panic if a matter or contact gets deleted. Go to File > Recycle Bin. Records can be retrieved from here.
- Time Matters gives you the ability to secure or hide a particular field, or allow only certain people to edit or view the field.
- To turn off the Alert’s, Reminders and Watches form upon login, go to File > Setup > General > User Level and uncheck the “Show Alerts and Reminders screen after login” box.
Wednesday, June 15, 2011
Do you have updates waiting?
Tuesday June 14, 2011 was Patch Tuesday. If your computer is not up to date, now is the time to install those Microsoft updates. Below describes pretty much what the latest release of updates will fix.
16 Bulletins, 34 Vulnerabilities, Lots of Patching |
Lately attackers have focused on leveraging web and browser-based vulnerabilities to install malware via "Drive-by Downloads." So you may want to install the Critical IE updates before the others.
Microsoft has posted their June Patch Day summary, which contains 16 security bulletins, nine of which they rate as Critical. The bulletins fix around 34 vulnerabilities in many Microsoft products, including:
Severity: High
Summary:
· These vulnerabilities affects: All current versions of Internet Explorer, running on all current versions of Windows
· How an attacker exploits it: Typically, by enticing one of your users to visit a malicious web page
· Impact: In the worst case an attacker can execute code on your user's computer, gaining complete control of it
· What to do: Deploy the appropriate Internet Explorer patches immediately, or let Windows Automatic Update do it for you
Exposure:
· MS11-050: IE Cumulative Update
Microsoft warns of 11 new IE vulnerabilities in their cumulative IE update. Though these 11 flaws differ technically, most of them (eight) share the same general scope and impact. They all involve memory corruption issues having to do with how IE handles various HTML elements, such as link properties and layout memory. If an attacker can lure one of your users to a web page containing malicious web code, he could exploit any one of these memory corruption vulnerabilities to execute code on that user's computer, inheriting that user's privileges. Typically, Windows users have local administrative privileges, in which case the attacker gains complete control of the victim's computer. Attackers often leverage these type of code execution vulnerabilities to launch Drive-by Download attacks.
The remaining issues cover less severe information disclosure vulnerabilities.
If you'd like to know more about the technical differences between these flaws, see the "Vulnerability Information" section of Microsoft's bulletin. Technical differences aside, the memory corruption flaws in IE pose significant risk. You should download and install the IE cumulative patch immediately.
· MS11-052: IE (and Windows) VML Code Execution Flaw
IE also suffers from a memory corruption vulnerability having to do with how it parses specially crafted Vector Markup Language (VML) that references uninitialized or deleted objects. By enticing one of your users to a specially crafted web page, an attacker could leverage this flaw to execute code on that user's computer, with their privileges. As usual, if the victim has local administrative privilege, the attacker gains complete control of the victim's computer. This flaw is similar in scope to previous VML IE flaws, like the one we demonstrate in this old Wire video.
Keep in mind, today's attackers commonly hijack legitimate web pages and booby-trap them with malicious code. Typically, they do this via hosted web ads or through SQL injection and XSS attacks. Even recognizable and authentic websites could pose a risk to your users if hijacked in this way.
Solution Path:
These patches fix serious issues. You should download, test, and deploy the appropriate IE patches immediately, or let Windows Automatic Update do it for you.
· Internet Explorer 6.0
o For Windows Server 2003 (w/SP2)
o For Windows Server 2003 x64 (w/SP2)
o For Windows Server 2003 Itanium (w/SP2)
· Internet Explorer 7.0
o For Windows Server 2003 (w/SP2)
o For Windows Server 2003 x64 (w/SP2)
o For Windows Server 2003 Itanium (w/SP2)
o For Windows Vista (w/SP1 or SP2)
o For Windows Vista x64 (w/SP1 or SP2)
o For Windows Server 2008 (w/SP2) *
o For Windows Server 2008 x64 (w/SP2) *
o For Windows Server 2008 Itanium (w/SP2)
· Internet Explorer 8.0
o For Windows Server 2003 (w/SP2)
o For Windows Server 2003 x64 (w/SP2)
o For Windows Vista (w/SP1 or SP2)
o For Windows Vista x64 (w/SP1 or SP2)
o For Windows Server 2008 (w/SP2) *
o For Windows Server 2008 x64 (w/SP2) *
o For Windows Server R2 2008 x64
o For Windows Server R2 2008 Itanium
· Internet Explorer 9.0
o For Windows Vista (w/SP1 or SP2)
o For Windows Vista x64 (w/SP1 or SP2)
o For Windows Server 2008 (w/SP2) *
o For Windows Server 2008 x64 (w/SP2) *
o For Windows Server R2 2008 x64 *
* Note: These flaws do not affect Windows Server 2008 administrators who installed using the Server Core installation option.
· Internet Explorer 6.0
o For Windows Server 2003 (w/SP2)
o For Windows Server 2003 x64 (w/SP2)
o For Windows Server 2003 Itanium (w/SP2)
· Internet Explorer 7.0
o For Windows Server 2003 (w/SP2)
o For Windows Server 2003 x64 (w/SP2)
o For Windows Server 2003 Itanium (w/SP2)
o For Windows Vista (w/SP1 or SP2)
o For Windows Vista x64 (w/SP1 or SP2)
o For Windows Server 2008 (w/SP2) *
o For Windows Server 2008 x64 (w/SP2) *
o For Windows Server 2008 Itanium (w/SP2)
· Internet Explorer 8.0
o For Windows Server 2003 (w/SP2)
o For Windows Server 2003 x64 (w/SP2)
o For Windows Vista (w/SP1 or SP2)
o For Windows Vista x64 (w/SP1 or SP2)
o For Windows Server 2008 (w/SP2) *
o For Windows Server 2008 x64 (w/SP2) *
o For Windows Server R2 2008 x64 *
o For Windows Server R2 2008 Itanium
* Note: These flaws do not affect Windows Server 2008 administrators who installed using the Server Core installation option.
Friday, June 3, 2011
Manage your Email better with Outlook 2010
If you haven’t already upgraded to the Windows 7 operating system, you might be interested to know that Outlook Express is not compatible with Windows 7. So the obviously thing to do is get yourself a copy of Microsoft Office which includes Outlook, Excel, PowerPoint, One Note and Word. For the purposes of this blog, I am only going to discuss Outlook. Outlook is very different from Outlook Express as far as features are concerned. For that matter, Outlook 2007 is very different from Outlook 2010. But let’s just say you want the latest version of Outlook 2010. And even if you have been using it already, you will find that there are a few things that might make life a little easier for you if you try them out.
Mail Tips
If you have ever had that sinking feeling of hitting “reply all” by mistake or maybe you sent some important information to someone only to learn later that their email address was invalid? Or maybe you sent some important information to someone only to learn later that their email address was invalid? Microsoft Exchange 2010 and Mail Tips can help prevent these embarrassing mistakes, save you time and alleviate your frustration. Learn about Mail Tips
Share your Calendar
Lawyers often want to share their calendar with staff. With Microsoft Exchange Server you can share your calendar. Or you can publish your calendar to the web which would allow more people to see it. Learn how to share you Calendar
Stop doing repetitive tasks
If you do a lot of the same things over and over when you are working with email, for example, move messages to a specific folder, Quick Steps in Outlook 2010 can help by turning commands and procedures that you use most often into one click actions. Learn about Quick Steps
Manage your conversations
You may have conversations over email where several people are discussing important issues. With Outlook 2010 you can see your email within the context of the conversation with conversation view. You can see the overall conversation, including your responses and also find the most recent response. Learn about Conversations
Ignore all Email messages in a conversation
If you are no longer needed in an email conversation you can prevent additional responses from appearing in your inbox. The ignore command moves the whole conversation and any future messages that arrive in the conversation to the deleted items folder. Learn how to ignore messages in a conversation
Let colleagues know when you aren’t around
If you have an Exchange account, when you are heading out on vacation or even just out of the office for the day, let your clients and colleagues know that you are out and when you will return with an automatic reply to their email. How to turn on automatic replies
Outlook Contacts
Thanks to Microsoft Outlook Global Address List (GAL) you no longer have to keep your contacts' information stored on your computer (where it takes up space). The Global Address List tracks it all for you: phone numbers, building location, email addresses and more.
Upgrading to Office 2010 can make you more efficient with regard to workflow. Keep in mind that with the Windows 7 operating system Outlook Express is no longer compatible. When purchasing new machines, you will have to upgrade your email if you have been using Outlook Express. Make sure you upgrade to Outlook 2010. Having an exchange server or using hosted exchange also benefits you in many ways. For example your email gets backed up daily and you have a larger capacity to store email. Also with hosted exchange if you lose power to your office you can still get your email on a laptop or your home computer. If you have any questions or would like to know more about your email options, we are happy to assist you. Give us a call at 516-762-0155.
Thursday, May 12, 2011
Important Office Updates for Microsoft PowerPoint
Severity: High
Summary:
· These vulnerabilities affect: Most current versions of Microsoft PowerPoint for Windows and Mac (ships with Office), except for 2010.
· How an attacker exploits it: By tricking one of your users into opening a malicious PowerPoint document
· Impact: In the worst case, an attacker executes code on the user's computer, gaining complete control of it
· What to do: Install Microsoft's PowerPoint updates as soon as possible, or let Microsoft's automatic update do it for you (Mac update not available yet)
Exposure:
If an attacker can entice one of your users into downloading and opening a maliciously crafted PowerPoint document, they can exploit either of these vulnerabilities to execute code on a victim's computer.
Attackers utilize malicious Office documents in their targeted email attacks (spear phishing). User often consider Office documents as benign. Yet, criminals can easily leverage these sorts of vulnerabilities to cause malicious office documents to install malware. We recommend, you install this updates as soon as you can.
Solution Path
Microsoft has released patches for the Windows version of PowerPoint to correct these vulnerabilities. You should download, test, and deploy the appropriate patches throughout your network immediately, or let the Microsoft Automatic Update feature do it for you.
Unfortunately, Microsoft has not yet released the Mac updates yet. They don't say exactly when they plan to release the Mac update, only that they will when testing is complete.
PowerPoint update for:
Office Compatibility Pack for Word, Excel, and PowerPoint 2007 File Formats
Tuesday, April 12, 2011
Microsoft Patch Day is here…
Microsoft released today 17 Security Bulletins. The updates fix security flaws in Windows, Office, .NET and Internet Explorer (IE), as well as some issues in some of Microsoft’s Server and Developer software.
More than half of the updates are rated as Critical by Microsoft – Critical generally mean attackers can leverage them to execute code on your computer, and gain control of it.
You should proactively install these Updates on Servers as Workstations as soon as possible.
Here is a link directly to the Patches: Microsoft Security Bulletins
If you have the Microsoft Windows Update Service enabled many of these updates may automatically get installed.
If you had our Patch Management Service you wouldn't have to worry about critical updates because they would be automatically installed for you. To find out more contact us.
Glasser Tech is a Full Service Technology Company based on Long Island, New York. We specialize in software, hardware and networking for small businesses. Our expertise is in the area of Law Office Automation. If you would like to know more about the services we offer call (516) 762-0155
Current State of Social Networks
Interesting trends in Social Media by Gender, Age, Education. Wealth.

Glasser Tech is a Full Service Technology Company based on Long Island, New York. We specialize in software, hardware and networking for small businesses. Our expertise is in the area of Law Office Automation. If you would like to know more about the services we offer call (516) 762-0155
Sunday, April 10, 2011
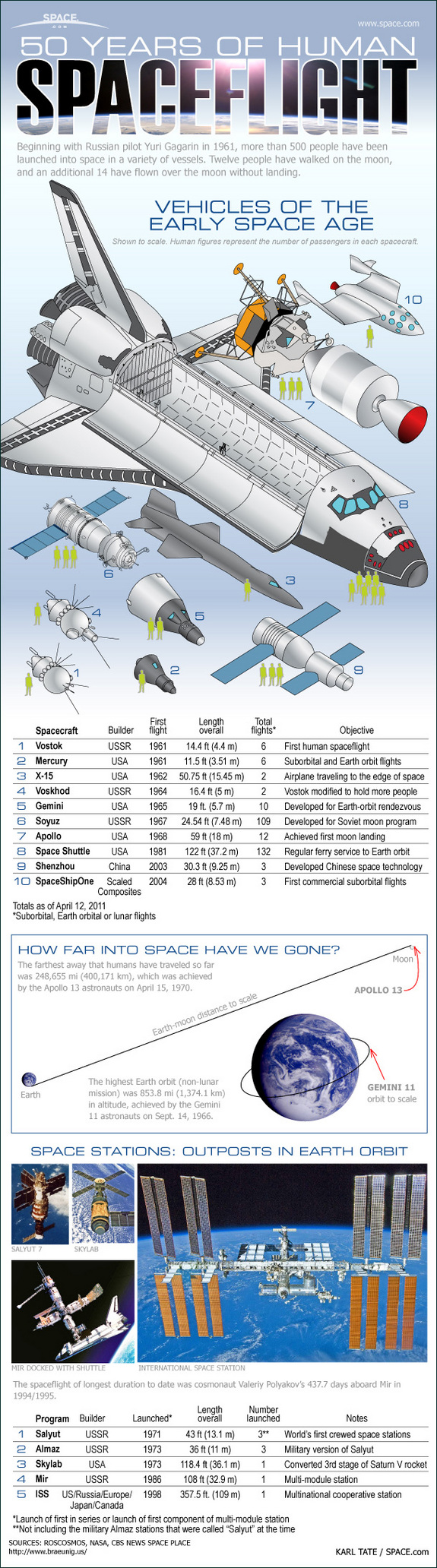
Celebrating 50 Years in Space
The graphic below is a History of Manned Space Travel -- created by SPACE.com
Click the link to see some great pictures: Astronaut Photos from Beyond Planet Earth
Glasser Tech is a Full Service Technology Company based on Long Island, New York. We specialize in software, hardware and networking for small businesses. Our expertise is in the area of Law Office Automation. If you would like to know more about the services we offer call (516) 762-0155
Saturday, April 9, 2011
Mobile Phone - Interesting Stats
Check out some interesting trends in Mobile Phone usage. Of the 4 Billion phones in use in the world I was surprised to find that more than 25% of them are smartphones. Mobile Marketing is the largest growth segment in Advertising.
Glasser Tech is a Full Service Technology Company based on Long Island, New York. We specialize in software, hardware and networking for small businesses. Our expertise is in the area of Law Office Automation. If you would like to know more about the services we offer call (516) 762-0155
Tuesday, April 5, 2011
Your Personal Information Has Most Likely Been Exposed to a Hacker
If you have not already, you most likely will, receive an email that your information may have been compromised due to a “Security Breach” (Hacked is more appropriate). Epsilon is the company whose data was exposed.
Who is Epsilon? They are the world’s largest provider of permission-based email marketing on behalf of some of the most well known companies.
The exposure is not just limited to the companies in the image above. At this point we do not know the full extent to which companies have been affected. The current list is a who’s who in business. Here is the list as I currently know it:
Target – Best Buy – Walgreen’s - Capital One – TiVo - JP Morgan Chase & Co. – Kroger - US Bank – Citi - McKinsey & Company - Ritz-Carlton Rewards - Marriott Rewards - New York & Company – Brookstone - The College Board - Home Shopping Network (HSN) - LL Bean - Disney Destinations - Barclays Bank of Delaware
Expect more companies to be added to the list as the extent of the damage becomes known.
Why is this important? The “Bad Guys” now have your name and e-mail address as well as information about where you shop, bank, etc.. With this information they will launch a “phishing” attack. In such an attack, an email, that purports to come from a legitimate business will try to trick you into clicking and acting on the information in the email. Don’t be fooled. These emails look real.
What can happen? If you act on the “phishing” attack there are a number of possibilities. You may accidentally give out personal information. You may infect your computer with spyware. Hackers can sometimes get full control of your PC and cull data for use in other attacks. Your identity may be stolen.
What should you do? In the best of possible worlds setup a new email address and change all your online accounts to the new email address. If you don’t want to do that then you need to be extremely cautious. If an email ever requests a password change or personal information do not click the links in that email. If you get a marketing email from your favorite store with a "too good to be true" offer, you may want to think twice before clicking the links.
I could imagine them sending an email like this: “We recently had a Security Breach and your email address and information may have been compromised. Click the link to our website and update your information." Never fall for that! If you have any question then pickup the phone and call. If a number is referenced in the email do NOT call that number. Get the number from the legitimate website or a different source other than the email.
If you get suspect emails forward them to: spam@uce.gov and reportphishing@antiphishing.org
Glasser Tech is a Full Service Technology Company based on Long Island, New York. We specialize in software, hardware and networking for small businesses. Our expertise is in the area of Law Office Automation. If you would like to know more about the services we offer call (516) 762-0155
Wednesday, March 30, 2011
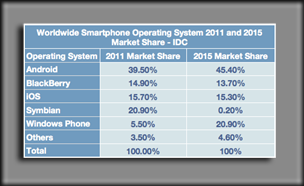
IDC Crystal Ball Smartphone Prediction
It will be interesting to look back in four years to see where the market stands. Right now the Android O/S appears to be the big winner. Apple needs to develop a lower-end device to be competitive so, don’t count them out as well. Let’s see if Research in Motion (RIM - BlackBerry) and Microsoft can make any major inroads against them.
Glasser Tech is a Full Service Technology Company based on Long Island, New York. We specialize in software, hardware and networking for small businesses. Our expertise is in the area of Law Office Automation. If you would like to know more about the services we offer call (516) 762-0155
Tuesday, March 29, 2011
Serve Mobile Payments by AmEx
 Monday American Express entered the game in the rapidly growing electronic payments arena with Serve.
Monday American Express entered the game in the rapidly growing electronic payments arena with Serve. Sunday, March 27, 2011
Pixel QI - Innovative Display Technology
 One of the main issues with display technology is that they work poorly in direct sunlight. Pixel Qi has come up with a display that works great indoors as well as outdoors. In addition to being highly readable the display can use up to 80% less power thus allowing for devices with a much greater battery life. They are licensing this technology called “Transflective 2.0” to hardware vendors. Look for devices with this innovative technology later this year.
One of the main issues with display technology is that they work poorly in direct sunlight. Pixel Qi has come up with a display that works great indoors as well as outdoors. In addition to being highly readable the display can use up to 80% less power thus allowing for devices with a much greater battery life. They are licensing this technology called “Transflective 2.0” to hardware vendors. Look for devices with this innovative technology later this year.For the latest information about Pixel Qi read their blog: http://www.pixelqi.com/blog1/
| If you would like to know more about the services we offer call (516) 762-0155 Visit our Website  |
Thursday, March 24, 2011
Microsoft Releases Security Advisory
This week Microsoft released a security advisory warning that one of their trusted Root Certification Authority Partners-Comodo, issued 9 fraudulent digital certificates for some very popular domains including:
- login.live.com
- mail.google.com
- login.yahoo.com
- login.skype.com
- addons.mozilla.org
- “Global Trustee”
While Comodo has already revoked the fraudulent certificates, Microsoft released a Windows update that revokes these signatures. If you have enabled automatic updates, you may have already received it. Otherwise be sure to click download and install it.
Michael Glasser's Linked In Page
Monday, March 21, 2011
Internet Explorer 9
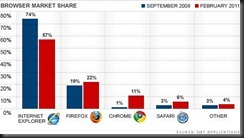 Microsoft recently released Internet Explorer 9. While Microsoft Internet Explorer is still the leading Internet browser they have been rapidly losing market share to the likes of Firefox, Google Chrome and even Apple's Safari.
Microsoft recently released Internet Explorer 9. While Microsoft Internet Explorer is still the leading Internet browser they have been rapidly losing market share to the likes of Firefox, Google Chrome and even Apple's Safari.
Interestingly Microsoft has forgone a large part of their market with this new release. Internet Explorer 9 (IE9) is only Compatible with Windows 7 & Windows Vista Computers. They chose not to provide support for all the computers running Windows XP – which is still almost about 50% of the computers running a Microsoft Windows Operating System. So for those of you running Windows XP skip the rest of this.
Top Internet Explorer 9 Features:
- Improved Performance – Implementing Hardware Acceleration IE9 is able to take full advantage of the processing power of todays computers. Websites become faster and more responsive.
- Streamlined Interface – The address bar, tabs, and navigation buttons are now on a single row.
- Tab Pinning: Tabs can be pinned to the Windows 7 task bar. Right click on the IE9 task bar icon to bring up a a menu of Pinned and Frequent Websites.
- Download Manager: Capability to manage downloaded files in a simple interface.
- Tracking Protection Lists: Allows the user to determine which websites to allow browsing tracking, and which sites to block that do not implement good privacy practices. NOTE: This feature is Off by Default. To turn it on Click Settings (The Gear Icon on the far right of the IE9 Toolbar) then Safety then Tracking Protection
- SmartScreen Filter: Verifies websites against Microsoft’s blacklist and blocks known malicious sites.
- Add-On Performance Advisor: Looks at your installed add-ons and tells you which ones are slowing your browser down the most and allows you to disable them.
Before installing IE9 check compatibility with any special websites you visit on a regular basis. Banking and Brokerage websites particularly could be of concern. I checked the LexisNexis Requirements for online Research and IE9 is not mentioned yet – this does not mean it will not work.
Internet Explorer 9 is a step in the right direction. With its new security and performance enhancements it is now on par with their main competitors Firefox and Google Chrome. I will have to use it more over the next couple of months and will reserve final judgment.
| If you would like to know more about the services we offer call (516) 762-0155 Visit our Website  |